Barcodes lasern und WLAN: Unterschied zwischen den Seiten
(Die Seite wurde neu angelegt: „Das Lasern von Barcodes, die hinterher auch lesbar sind, erfordert einige zusätzliche Schritte – diese Anleitung soll dir dabei behilflich sein. Zunächst e…“) |
|||
| Zeile 1: | Zeile 1: | ||
| − | + | We're moving our wifi infrastructure to an authenticated and encrypted ssid. At the moment it's hard to change our internal wifi password, because our door system depends on it. If you are not in our internal wifi you can't operate the door. | |
| − | + | This is one reason why we want to use 802.1x with EAP-TTLS. Every member has it's own username/password combination which can be reset or changed through a webinterface. If a member quits the space, we just have to deactivate the account and the internal access is gone. | |
| − | + | The other reason is: Every member has its own encrypted channel to our access points. In addition the member has the possibility to check, if the SSID can be trusted (avoid roque APs) with an ssl certificate | |
| − | + | == certificate == | |
| − | [ | + | To check if you're connecting to the correct SSID, you can and should add the ssl certificate to your connection setting. You can download the [https://www.hackerspace-bamberg.de/bckspc-downloads/bckspc-ca.crt SSL CA-Certificate] ([https://www.hackerspace-bamberg.de/bckspc-downloads/bckspc-ca.zip ZIP-File]) from our Server. |
| − | + | == netctl == | |
| − | + | Save config as /etc/netctl/$interfacename-backspace_8021x. You have to restart netctl-auto (e.g. systemctl restart netctl-auto@$interface) | |
| − | + | <syntaxhighlight line enclose="div"> | |
| + | Description='backspace WPA2 802.1X' | ||
| + | Interface=wlp3s0 | ||
| + | Connection=wireless | ||
| + | Security=wpa-configsection | ||
| + | IP=dhcp | ||
| + | ESSID="backspace 802.1x" | ||
| + | WPAConfigSection=( | ||
| + | 'ssid="backspace 802.1x"' | ||
| + | 'proto=RSN WPA' | ||
| + | 'key_mgmt=WPA-EAP' | ||
| + | 'eap=TTLS' | ||
| + | 'identity="USERNAME"' | ||
| + | 'password="YOUR_PASSWORD"' | ||
| + | 'ca_cert="hash://server/sha256/3e8977b8a92cc0be99b940323a2125fc2032727074a282d066801ee9dc3a2d97"' | ||
| + | 'phase2="auth=PAP"' | ||
| + | ) | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | FYI: Replace the interface name according to your system | ||
| + | |||
| + | == wpa_supplicant == | ||
| + | |||
| + | Add to '''/etc/wpa_supplicant/wpa_supplicant.conf''': | ||
| + | |||
| + | <syntaxhighlight line enclose="div"> | ||
| + | network={ | ||
| + | ssid="backspace 802.1x" | ||
| + | key_mgmt=WPA-EAP | ||
| + | eap=TTLS | ||
| + | identity="USERNAME" | ||
| + | password="YOUR_PASSWORD" | ||
| + | phase2="auth=PAP" | ||
| + | ca_cert="hash://server/sha256/3e8977b8a92cc0be99b940323a2125fc2032727074a282d066801ee9dc3a2d97" | ||
| + | } | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | == connman == | ||
| + | |||
| + | '''UNTESTED!''' | ||
| + | |||
| + | <syntaxhighlight line enclose="div"> | ||
| + | [service_backspace] | ||
| + | Type=wifi | ||
| + | Name="backspace 802.1x" | ||
| + | EAP=ttls | ||
| + | Phase2=PAP | ||
| + | Identity=USERNAME | ||
| + | Passphrase=YOUR_PASSWORD | ||
| + | CACertFile = hash://server/sha256/3e8977b8a92cc0be99b940323a2125fc2032727074a282d066801ee9dc3a2d97 | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | '''Sailfish OS''' | ||
| + | |||
| + | Tested and working | ||
| + | |||
| + | Put the following into /var/lib/connman/wifi_bckspc-8021x.config | ||
| + | |||
| + | then | ||
| + | |||
| + | systemctl restart connman | ||
| + | |||
| + | <syntaxhighlight line enclose="div"> | ||
| + | [service_backspace] | ||
| + | Type = wifi | ||
| + | Name = backspace 802.1x | ||
| + | EAP = ttls | ||
| + | Phase2 = PAP | ||
| + | Identity = USERNAME | ||
| + | Passphrase = PASSWORD | ||
| + | CACertFile = hash://server/sha256/3e8977b8a92cc0be99b940323a2125fc2032727074a282d066801ee9dc3a2d97 | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | == wicd == | ||
| + | |||
| + | <syntaxhighlight line enclose="div"> | ||
| + | ctrl_interface=/var/run/wpa_supplicant | ||
| + | network={ | ||
| + | ssid="backspace 802.1x" | ||
| + | scan_ssid=$_SCAN | ||
| + | identity="USERNAME" | ||
| + | password="YOUR_PASSWORD" | ||
| + | proto=WPA2 | ||
| + | key_mgmt=WPA-EAP | ||
| + | group=CCMP | ||
| + | pairwise=CCMP | ||
| + | eap=TTLS | ||
| + | anonymous_identity="$_ANONYMOUS_IDENTITY" | ||
| + | phase2="auth=PAP" | ||
| + | ca_cert="hash://server/sha256/3e8977b8a92cc0be99b940323a2125fc2032727074a282d066801ee9dc3a2d97" | ||
| + | } | ||
| + | </syntaxhighlight> | ||
| + | |||
| + | '''Warning:''' This is not yet tested. ca_cert certificate checking should work as it does for netctl and wpa_supplicant. Adapted from [https://events.ccc.de/congress/2014/wiki/Static_Talk%3ANetwork 31c3 wiki] | ||
| + | |||
| + | == Android == | ||
| + | |||
| + | This is how you can connect with the android operating system to our 802.1x WIFI (WPA2 Enterprise) | ||
| + | |||
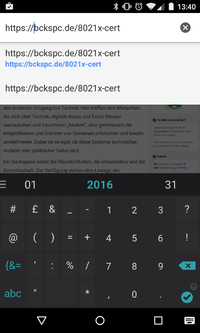
| + | * Download our certificate at http://bckspc.de/8021x-cert | ||
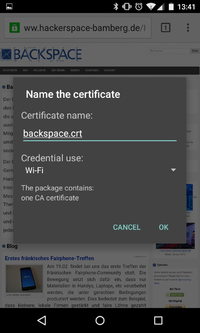
| + | * Open downloaded certificate | ||
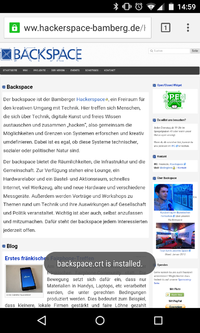
| + | * Save certificate as backspace.crt and type "Wifi" | ||
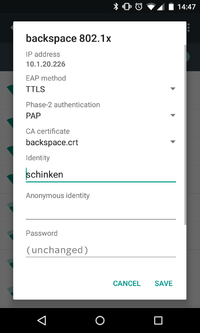
| + | * Modify/Configure your backspace 802.1x connection according to the screenshot below | ||
| + | * '''Attention:''' Some newer Android versions require a domain name if you use the certificate. Use '''radius.core.bckspc.de''' | ||
| + | * Firefox on android might fail to import the certificate, stating that the certificate authority is already trusted. In these cases, chrome can stil import the certificate. | ||
| + | |||
| + | [[Datei:8021x-android-1.png|200px]] [[Datei:8021x-android-2.png|200px]] [[Datei:8021x-android-3.png|200px]] [[Datei:8021x-android-4.png|200px]] | ||
| + | |||
| + | == Linux - NetworkManager == | ||
| + | |||
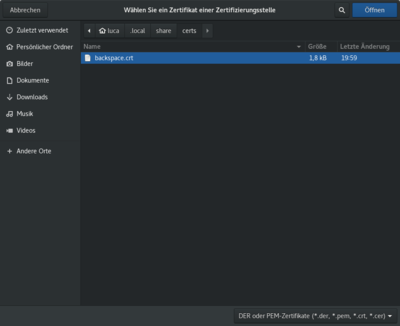
| + | * Download the [[#certificate|certificate]] | ||
| + | * Select the "backspace 802.1x" network in your WiFi settings | ||
| + | * Select the previously downloaded certificate | ||
| + | *: [[Datei:Linux NetMan Certificate.png|400px]] | ||
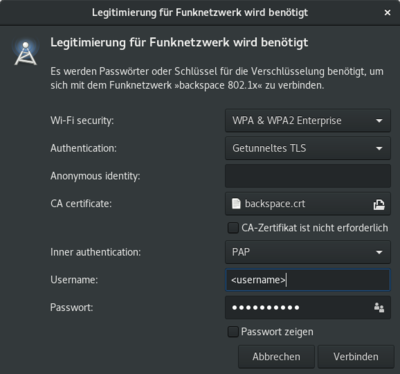
| + | * Select "TTLS" and "PAP" as the authentication and inner authentication method, respectively (see below) | ||
| + | * Fill in your username and password (see below) | ||
| + | |||
| + | [[Datei:Linux NetMan Authentication.png|400px]] | ||
| + | |||
| + | == macOS and iOS == | ||
| + | |||
| + | '''A ready profile file can be downloaded [[:File:Backspace802.1x.mobileconfig.zip|here]] (you need to provide your LDAP credentials when asked). You don't need to follow the other steps if you use this file.''' Note: For iOS you need to extract this ZIP file and send it to you phone (e.g. via email). | ||
| + | |||
| + | ---- | ||
| + | |||
| + | The following procedure has been tested using macOS 10.11 El Capitan to macOS 10.14 Mojave. | ||
| + | |||
| + | Earlier versions of macOS offered to specify the authentication protocol when connecting to a wireless network. However, in newer versions you'll have to install a configuration profile in order to connect to our network using 802.1X with EAP-TTLS/PAP. This configuration profile contains our certificate and all required settings. | ||
| + | |||
| + | It is fairly easy to generate a configuration file for your devices yourself with the added bonus of already including your username and password. This file can be used for all your Macs and iOS devices. | ||
| + | |||
| + | To generate the config file you need to download the Apple Configurator from the Mac App Store. [https://itunes.apple.com/de/app/apple-configurator-2/id1037126344?mt=12] | ||
| + | |||
| + | Start the Configurator and choose File -> New Profile | ||
| + | |||
| + | In the General tab give the profile a name. | ||
| + | |||
| + | Then go down to Wi-Fi and configure the Payload: | ||
| + | |||
| + | SSID: backspace 802.1x<br /> | ||
| + | Security: Enterprise WPA2<br /> | ||
| + | EAP-TTLS<br /> | ||
| + | you can add your username and password here<br /> | ||
| + | Inner Authentification: PAP<br /> | ||
| + | |||
| + | Choose Save from the File menu and give the profile a name. | ||
| + | |||
| + | You can now install the profile on your Mac. (The installation only seems to work, if you have installed the Certificate under "Certificates" in the Configurator. But you must not click the certificate under "Trust" in the Wi-Fi payload, because that will fail the authentification. See below for trusting the RADIUS server.) | ||
| + | |||
| + | To install the file on your iOS device, simply connect the device to the laptop running Configurator via USB and drag the profile file onto the device when it shows up in the application. | ||
| + | |||
| + | Alternatively you can send the file to yourself via email. Tap the file in the Mail app and install it on your iOS device. '''WARNING''': This will likely send your credentials '''unencrypted''' through the internet! | ||
| + | |||
| + | When installing your profiles the systems will tell you that the certificate is not signed and that you need to trust the RADIUS server. You just need to accept both and are ready. | ||
| + | |||
| + | == Windows 8 and above == | ||
| + | |||
| + | Since Windows 8 the system itself is capable of EAP-TTLS. | ||
| + | |||
| + | TODO: Someone with windows should do some screenshots. | ||
Version vom 14. November 2019, 00:10 Uhr
We're moving our wifi infrastructure to an authenticated and encrypted ssid. At the moment it's hard to change our internal wifi password, because our door system depends on it. If you are not in our internal wifi you can't operate the door.
This is one reason why we want to use 802.1x with EAP-TTLS. Every member has it's own username/password combination which can be reset or changed through a webinterface. If a member quits the space, we just have to deactivate the account and the internal access is gone.
The other reason is: Every member has its own encrypted channel to our access points. In addition the member has the possibility to check, if the SSID can be trusted (avoid roque APs) with an ssl certificate
certificate
To check if you're connecting to the correct SSID, you can and should add the ssl certificate to your connection setting. You can download the SSL CA-Certificate (ZIP-File) from our Server.
netctl
Save config as /etc/netctl/$interfacename-backspace_8021x. You have to restart netctl-auto (e.g. systemctl restart netctl-auto@$interface)
Description='backspace WPA2 802.1X'
Interface=wlp3s0
Connection=wireless
Security=wpa-configsection
IP=dhcp
ESSID="backspace 802.1x"
WPAConfigSection=(
'ssid="backspace 802.1x"'
'proto=RSN WPA'
'key_mgmt=WPA-EAP'
'eap=TTLS'
'identity="USERNAME"'
'password="YOUR_PASSWORD"'
'ca_cert="hash://server/sha256/3e8977b8a92cc0be99b940323a2125fc2032727074a282d066801ee9dc3a2d97"'
'phase2="auth=PAP"'
)FYI: Replace the interface name according to your system
wpa_supplicant
Add to /etc/wpa_supplicant/wpa_supplicant.conf:
network={
ssid="backspace 802.1x"
key_mgmt=WPA-EAP
eap=TTLS
identity="USERNAME"
password="YOUR_PASSWORD"
phase2="auth=PAP"
ca_cert="hash://server/sha256/3e8977b8a92cc0be99b940323a2125fc2032727074a282d066801ee9dc3a2d97"
}connman
UNTESTED!
[service_backspace]
Type=wifi
Name="backspace 802.1x"
EAP=ttls
Phase2=PAP
Identity=USERNAME
Passphrase=YOUR_PASSWORD
CACertFile = hash://server/sha256/3e8977b8a92cc0be99b940323a2125fc2032727074a282d066801ee9dc3a2d97Sailfish OS
Tested and working
Put the following into /var/lib/connman/wifi_bckspc-8021x.config
then
systemctl restart connman
[service_backspace]
Type = wifi
Name = backspace 802.1x
EAP = ttls
Phase2 = PAP
Identity = USERNAME
Passphrase = PASSWORD
CACertFile = hash://server/sha256/3e8977b8a92cc0be99b940323a2125fc2032727074a282d066801ee9dc3a2d97wicd
ctrl_interface=/var/run/wpa_supplicant
network={
ssid="backspace 802.1x"
scan_ssid=$_SCAN
identity="USERNAME"
password="YOUR_PASSWORD"
proto=WPA2
key_mgmt=WPA-EAP
group=CCMP
pairwise=CCMP
eap=TTLS
anonymous_identity="$_ANONYMOUS_IDENTITY"
phase2="auth=PAP"
ca_cert="hash://server/sha256/3e8977b8a92cc0be99b940323a2125fc2032727074a282d066801ee9dc3a2d97"
}Warning: This is not yet tested. ca_cert certificate checking should work as it does for netctl and wpa_supplicant. Adapted from 31c3 wiki
Android
This is how you can connect with the android operating system to our 802.1x WIFI (WPA2 Enterprise)
- Download our certificate at http://bckspc.de/8021x-cert
- Open downloaded certificate
- Save certificate as backspace.crt and type "Wifi"
- Modify/Configure your backspace 802.1x connection according to the screenshot below
- Attention: Some newer Android versions require a domain name if you use the certificate. Use radius.core.bckspc.de
- Firefox on android might fail to import the certificate, stating that the certificate authority is already trusted. In these cases, chrome can stil import the certificate.
Linux - NetworkManager
- Download the certificate
- Select the "backspace 802.1x" network in your WiFi settings
- Select the previously downloaded certificate
- Select "TTLS" and "PAP" as the authentication and inner authentication method, respectively (see below)
- Fill in your username and password (see below)
macOS and iOS
A ready profile file can be downloaded here (you need to provide your LDAP credentials when asked). You don't need to follow the other steps if you use this file. Note: For iOS you need to extract this ZIP file and send it to you phone (e.g. via email).
The following procedure has been tested using macOS 10.11 El Capitan to macOS 10.14 Mojave.
Earlier versions of macOS offered to specify the authentication protocol when connecting to a wireless network. However, in newer versions you'll have to install a configuration profile in order to connect to our network using 802.1X with EAP-TTLS/PAP. This configuration profile contains our certificate and all required settings.
It is fairly easy to generate a configuration file for your devices yourself with the added bonus of already including your username and password. This file can be used for all your Macs and iOS devices.
To generate the config file you need to download the Apple Configurator from the Mac App Store. [1]
Start the Configurator and choose File -> New Profile
In the General tab give the profile a name.
Then go down to Wi-Fi and configure the Payload:
SSID: backspace 802.1x
Security: Enterprise WPA2
EAP-TTLS
you can add your username and password here
Inner Authentification: PAP
Choose Save from the File menu and give the profile a name.
You can now install the profile on your Mac. (The installation only seems to work, if you have installed the Certificate under "Certificates" in the Configurator. But you must not click the certificate under "Trust" in the Wi-Fi payload, because that will fail the authentification. See below for trusting the RADIUS server.)
To install the file on your iOS device, simply connect the device to the laptop running Configurator via USB and drag the profile file onto the device when it shows up in the application.
Alternatively you can send the file to yourself via email. Tap the file in the Mail app and install it on your iOS device. WARNING: This will likely send your credentials unencrypted through the internet!
When installing your profiles the systems will tell you that the certificate is not signed and that you need to trust the RADIUS server. You just need to accept both and are ready.
Windows 8 and above
Since Windows 8 the system itself is capable of EAP-TTLS.
TODO: Someone with windows should do some screenshots.